Table of contents
Summary I
Abstract I
Chapter 1 Introduction 1
1.1 Research background and significance of the topic 1
1.2 Research status at home and abroad 3
1.3 Contents of this article 8
1.4 Structural arrangement 10
Chapter 2 Related Knowledge and Technology 11
2.1 Blockchain related knowledge 11
2.1.1 Blockchain 11
2.1.2 Ethereum 15
2.2 Knowledge related to cryptography 18
2.2.1 Algebra knowledge 18
2.2.2 ElGamal cryptosystem 18
2.2.3 Secure multi-party computation 20
2.2.4 Threshold cryptography system 22
2.2.5 Verifiable Secret Sharing Protocol VSS 22
2.2.6 Zero-knowledge proof of same exponent SEZ 23
Chapter 3 Secure Electronic Voting Solution 24
3.1 Electronic voting process 24
3.2 Security analysis of electronic voting 25
3.3 Improved protocol 25
3.3.1 Threshold Blind Signature Protocol TBS 26
3.3.2 Verifiable threshold decryption protocol VTC 27
3.4 Symbol description 29
3.4.1 Security Assumptions 29
3.4.2 Entities and symbols 29
3.5 Overview of the voting process 30
3.6 Details of the voting process 31
3.6.1 Preparation phase 31
3.6.2 Key sharing phase 32
3.6.3 Signature phase 32
3.6.4 Voting phase 32
3.6.5 Counting phase 32
3.7 Security and performance analysis 33
3.7.1 Security Analysis 33
3.7.2 Performance Analysis 34
3.7.3 Performance improvements 35
Chapter 4 System Design 36
4.1 Requirements analysis 36
4.1.1 Classification of participants 36
4.1.2 Use case form 37
4.1.3 Non-functional requirements 40
4.2 Overall design 40
4.2.1 System framework 41
4.2.2 Interface design 43
Chapter 5 System Implementation 45
5.1 Environment setup 45
5.2 Basic algorithm 45
5.3 Detailed design 47
5.3.1 Management module design 47
5.3.2 Key sharing module design 49
5.3.3 Voting module design 49
5.3.4 Vote counting module design 52
5.3.5 Query module design 54
5.4 Experimental analysis 55
5.4.1 Threshold performance analysis 56
5.4.2 Smart contract gas analysis 57
Chapter 6 Summary and Outlook 58
6.1 Summary 58
6.2 Outlook 58
Reference 59
Acknowledgments 66
1.3 Contents of this article
In 1992, Fujioka et al. [17] proposed a blind signature voting scheme (FOO) for large-scale elections and proposed seven electronic voting security standards. The program consists of 6 phases.
1. Preparation stage: Voter Vi chooses vi, and the encryption is xi=enc(vi,ki), where ki is a random value, enc() is the encryption algorithm?xi’=binde(xi,r)?e is the certification authority A Of the public key, r is a blinding factor? si=Signi(xi’) is Vi’s own signature, where Sign() is the signature function?
2. Management stage: Voters send (xi’, si) to A?A’s signature to get di=SignA(xi’), send signature di to Vi, and publish IDi, xi’, di
3. Voting stage: The voter uses the unblinding function undblind() to obtain yi=unblind(di,r), yi is A’s signature about xi, and sends (xi,yi) anonymously to the counting agency C
4. Collection phase: C verifies xi, yi, and publishes l, xi, yi. Where l is the serial number of (xi, yi) in the list
5. Public stage: Vi checks the information published by A and C and sends (l, ki) to C anonymously
6. Counting stage: C decrypts vi and counts it, and discloses l, xi, yi, ki, vi
3.1 Electronic voting process
Generally speaking, a complete electronic voting mainly goes through four stages: preparation stage, certification stage, voting stage and vote counting stage.
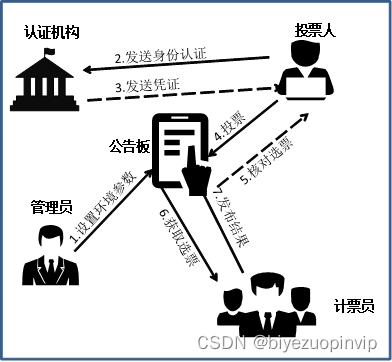
Figure 3.1 Electronic voting flow chart
Figure 3.1 shows that the completion of the voting process requires the cooperation of multiple parties. Voters are the main subjects of voting. Certification agencies issue voting vouchers to voters. Administrators are responsible for setting environmental parameters. Counters sing votes and announce winners. There are even arbitration institutions involved in handling election disputes. Overall the voting process is as follows. Preparation stage: The administrator publishes security parameters and other environmental parameters on the Bulltine Board, publishes a list of candidates, and sets time nodes for each stage and other information (step 1); Authentication stage: Voters provide identification information and are certified After successful institutional verification, legal voting vouchers or signatures are obtained (steps 2-3); voting stage: the voter encrypts the candidate options and sends them to the bulletin board together with the voucher or signature, and verifies from the bulletin board that the votes have been added correctly (steps 4-5); Counting stage: After the voting, the counters decrypt the ballots, count the votes of each candidate, and publish the election results on the bulletin board (steps 6-7).
The division of voting into four stages is not absolute. In actual system design, there may not be clear dividing lines between each stage. According to needs, multiple stages can be integrated, and a certain stage can also be subdivided.
# -*- coding:UTF-8 -*-
"""
Run time detection
"""
from .alg.ECC import *
from .alg.shamir import FVSS
from .vote_role import *
import datetime
import random
import pickle
# from database import models
#p=79432034159157298566448255051786468940817438396448206020190420091586587025641
#voternumberL
VN=1000000
candidate_list=[1,VN]
vote_num=1
SA_n=3
SA_t=2
TA_n=3
TA_t=2
def save(var):
""" with open('text.txt', 'wb') as file:
pickle.dump(var, file) """
var_pkl = pickle.dumps(var)
state=models.Dictionary.objects.filter(name="state")
if state.exists():
if state.first().value != var_pkl:
state.update(value=var_pkl)
if state.exists() == False:
state.create(name = "state", value = var_pkl, description = var)
def read():
""" with open('text.txt', 'rb') as file2:
var2 = pickle.load(file2)
return var2 """
state=models.Dictionary.objects.filter(name="state")
assert state.exists() , "Data does not exist!"
var = pickle.loads(state)
def test1():
state=State()
save(state)
state=read()
state=interface_SA_key_share(state,SA_n,SA_t)
save(state)
state=read()
state=interface_TA_key_share(state,TA_n,TA_t)
save(state)
state=read()
for i in range(vote_num):
state,vote=interface_choose_candidate(state,SA_n,SA_t,random.choice(candidate_list))
save(state)
state=read()
state,vote=interface_calculate_signature(state,vote)
save(state)
state=read()
state,subkey=interface_send_subkey(state,TA_n,TA_t)
save(state)
state=read()
interface_tally_result(state)
def test2():
#######################################Key distribution process###### #################
state = State()
state_db = state.blockchain
sa=State(state_db).SA()
state_db = state.blockchain;sa_db = sa.db
ta=State(state_db).TA()
state_db = state.blockchain;ta_db = ta.db
#################################################sign process#################
voters=[]
for i in range(1):
r=sa.choose_k() #Send r
voters.append(State().Voter(4,3))
e=voters[i].send_param(r,vote=random.choice(candidate_list))#Send e
s=sa.send_SK(e)#Send s
assert voters[i].verify(s)#voter verification s
vote=voters[i].compute_S(s)#Voters calculate signatures
###########################################Voting Process#### ###################
contract_vote=State().ContractVote()
assert contract_vote.verify_votes()#Vote contract verification signature
########################################Vote counting process###### ####################
#begin1=datetime.datetime.now()
contract_tally=State().ContractTally(4,3)#When the vote counting contract is initialized, perform homomorphic encryption
#end1=datetime.datetime.now()
ta.send_SK()#The counting agency sends the key
#begin2 = datetime.datetime.now()
contract_tally.verify_TA()#Verify the vote counting agency
M=contract_tally.compute_plain()#The vote counting contract calculates the decrypted sum
#end2 = datetime.datetime.now()
contract_tally.tally_result(M)#Vote counting contract calculation result
#return end1 - begin1
def test4():
state = State()
state.set_SAParam(3,2)
state.set_TAParam(4,3)
state_db = state.blockchain
sa=State(state_db).SA()
state_db = state.blockchain;sa_db = sa.db
ta=State(state_db).TA()
state_db = state.blockchain;ta_db = ta.db
#######
state = State(state_db)
sa=state.SA(sa_db)
r=sa.choose_k() #Send r
voter = state.Voter()
e=voter.send_param(r,vote=random.choice(candidate_list))#Send e
s=sa.send_SK(e)#Send s
assert voter.verify(s)#Voter verification s
vote=voter.compute_S(s)#Voter calculates signature
state_db = state.blockchain;sa_db = sa.db;voter_db=voter.db
#######
state = State(state_db)
contract_vote=state.ContractVote()
assert contract_vote.verify_votes()#Vote contract verification signature
state_db = state.blockchain
######
#begin1=datetime.datetime.now()
state = State(state_db)
contract_tally=state.ContractTally()#When the vote counting contract is initialized, perform homomorphic encryption
#end1=datetime.datetime.now()
ta = state.TA(ta_db)
ta.send_SK()#The counting agency sends the key
# begin2 = datetime.datetime.now()
contract_tally.verify_TA()#Verify the vote counting agency
M=contract_tally.compute_plain()#The vote counting contract calculates the decrypted sum
#end2 = datetime.datetime.now()
contract_tally.tally_result(M)#Vote counting contract calculation result
#return end1 - begin1
def runedTime():
begin = datetime.datetime.now()
test4()
end = datetime.datetime.now()
return end-begin
print(runedTime())
#test4()
#print(SA_n)



























